 da/sec scientific talk on Biometrics
da/sec scientific talk on Biometrics
Topic: Can impersonation be a real threat to spreaker recognition systems?
by Hareesh Mandalapu
D19/2.03a, December 06, 2018 (Thursday), 12.00 noon
Keywords — voice impersonation, spoof detection, speaker recognition
Abstract
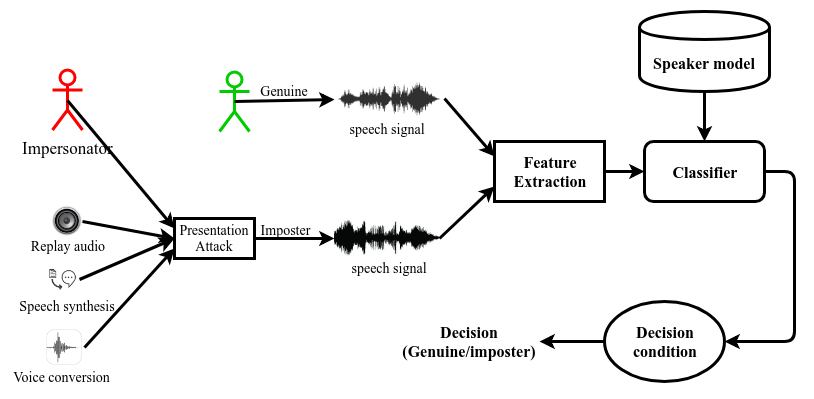
Speaker recogntion systems are vulnerable to spoofing techniques. Well-known voice spoofing methods are impersonation, replays, voice conversion, and speech synthesis. Among these, voice impersonation is the most obvious way of spoofing speaker recognition systems. Impersonators can mimic the target speaker’s voice after significant attempts without computer-aided technologies. Though impersonation is not considered as a serious threat for Automatic Speaker Verification (ASV) systems, studies show that professional impersonators can successfully alter the performance of classical systems of GMM-UBM and i-vector based methods. In this work, a database consisting of popular celebrity speeches and their impersonations is developed from youtube. The vulnerability of speaker recognition is evaluted. Though, the decrease in performance is observed, further work is required to prove that impersonation could be a serious problem.
